Whether you’ve been using Workday for a month or a few years, there’s always a lot to learn when it comes to making the most of any cloud-based software. One area of Workday functionality that will require your particular attention? Security permissions, dealing with sensitive data, personal data, and more.
This article will discuss the key components and capabilities of the Workday Security solution and where our team of Workday consultants can come in to help.
Understanding the Role-Based Security Group in Workday
The data in your Workday platform is critical to your company—not only in terms of your business itself but also the people who keep that business running.
That’s why protecting your customer’s personal data and ensuring it complies with regulations is a priority for every intelligent business. Of course, dealing with data privacy and sensitive data protection is sometimes easier said than done, especially when evolving security threats and ever-changing guidelines are considered.
Trying to balance the tasks of your data processor and data controller while keeping track of certain data that requires a unique encryption key can be challenging, especially while also trying to implement or integrate Workday modules into your system. Not sure how to navigate having so many aspects of data organization and security at once? That’s where you need a trusted Workday security administrator.
Here’s a library analogy to better explain how a role-based security group works in Workday.
How Does Security in Workday Work?
For this example, think of employees as having a login that lets them borrow a book from any library branch in the network so long as Workday security grants the employee access to that book. The library network is set up to have different kinds of data (or “books”) in each region, as demonstrated in the map below.
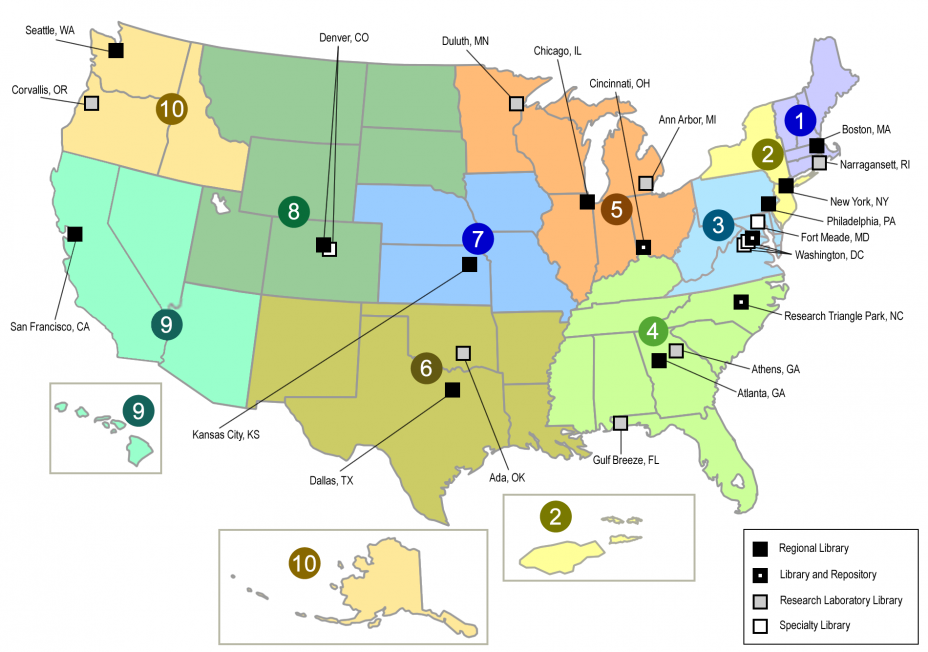
Here’s how some of your data may be stored and separated. (Note: This is a simplified example. Workday has hundreds of data domains.)
- Region 1 – Payroll Data
- Region 3 – Personal Contact Information and Demographics
- Region 4 – Compensation
- Region 9 – Job history records
- Region 10 – Benefits data and history
If we’re talking about the average employee, one with no additional designated HR or payroll security access, they can access books about themselves but wouldn’t be able to “sign out a book” about a coworker. On the other hand, some data on other workers in the company (such as name, job title, department, location, work phone, work email, and photo) are treated as “generally available” and don’t require particular security standards and guidelines.
A Real-Life Example
Let’s consider a manager. Managers could access Job and Compensation (Regions 9 and 4) information on their direct or indirect reports, but NOT Payroll Data in Region 1. Why? Because this data includes information on benefits (the deductions, which are indicative of benefit elections) and payroll-specific information (such as wage garnishments).
It’s not the manager’s business to know how much employees contribute to retirement or whether they have a child-support order garnishing their wages. A manager may have access to more data than non-managerial employees, but they don’t have unlimited access, especially regarding their employees’ most sensitive data.
Understanding Workday Security Roles
Whether you’re new to Workday or have been live for a while now, customer data, compliance requirements, and processing activities are ever-changing, and your team needs to be able to keep up with them.
One critical piece of the puzzle for your organization is ensuring all employees have access to the data and functionality needed to do their jobs. Not only do they need the ability to access specific data in the system, but it’s also essential to ensure that sensitive data doesn’t end up in the wrong hands.
This is where a role-based security group in Workday can come into play.
What Exactly Are They?
Security roles in Workday Security help your organization and its administrators stay on top of the continuous monitoring of data in and out of the system. They control an employee’s ability to update data, approve cross-border data transfers, initiate processing activities, and their security permissions in general.
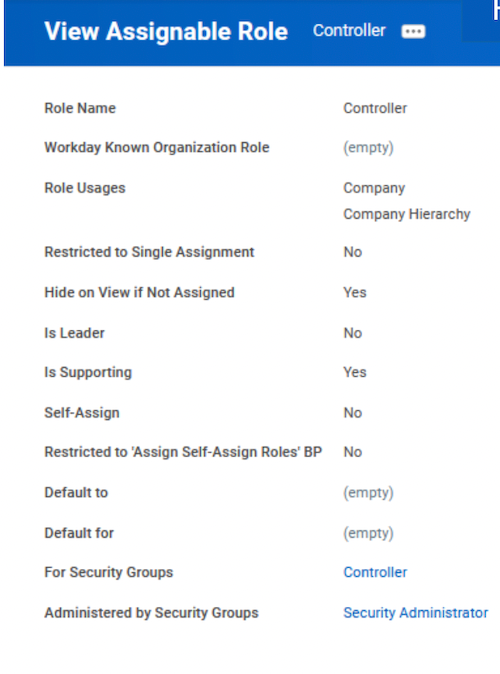
Although they are similar to your organization’s general data protection regulation processes, security roles in Workday outline each employee’s specific ability to access data, reports, and other insights and functions within your organization.
How Are They Different?
Security roles in Workday Security are determined and separated by an employee’s position rather than by each person specifically. This way, if employees leave your organization or move positions, it’s a little easier for you to navigate the security challenges that come with those changes.
Let’s say, for example, your current HR Manager gets promoted to CHRO. Rather than going into the Workday system and updating all kinds of security preferences for that person, they will inherit the Workday security roles associated with their new position, and the new HR Manager will do the same.
Cutting out unnecessary steps required for employee changes, security updates, or data transfers and protecting your sensitive data every step of the way. That’s the goal of a role-based security group in Workday.
Making Changes to Workday Security
Let’s think a little more about the security implications of when you need to change data in your Workday system. That’s when you must pay special attention to the intersection of Workday Security and Business Processes.
In addition to defining what happens in your Workday organization, such as validation, approvals, and notifications, your business processes also determine who can initiate a transaction, see a change in-flight (before it’s fully approved and committed to the database), undo the changes and restore values to their previous state, and do approvals.
However, certain kinds of data must be changed through a Task instead of a Business Process. Tasks—such as adding a new cost center—are administrative, so the user can take that action if someone is a member of a security group that can perform that task.
For example, imagine a “Cost Center Administrator.” A Cost Center Admin is usually someone in Finance who coordinates these changes with the General Ledger reference tables. As such, it’s appropriate for them to be able to securely add, edit, or deactivate a cost center.
NOTE: Approvals and notifications are not configurable for tasks.
Remember that redefining how Workday-delivered security operates in your organization is fine, so long as A) Management signs off on those changes and B) your audit team can find a trail of the request, management approval of the said request, testing, approval/acceptance of testing, release to production, and verification of release to production.
Creating Security Groups in Workday
Another way to optimize your Workday security features is to create layers of security that work in tandem with each other. For example, let’s say you have an employee working in Sales Ops who has no direct reports. Still, you’d like that person to be able to see compensation, including commissions, but only for salespeople.
One way to set that up would be to create a new custom security group, add the Sales Ops people to that security group, and apply to that group a set of security rules that allows access to compensation data for employees who have a compensation plan assigned to them that will enable payments of commissions. That way, you’re defining security not by domain or management hierarchy but by compensation plan assignment. Why is that useful?
Let’s pretend that our example employee moved from Sales to Marketing. Their former Sales coworkers no longer need access to their compensation information, and as soon as they leave the Sales Ops group in Workday—boom! That data is no longer accessible to their former peers, just like in our library analogy.
Workday Security Best Practices to Keep in Mind
Now that you have a better understanding of Workday security basics, here are a few best practices to keep in mind to help you use it effectively.
Below are a few of our recommended Workday security best practices:
- Review user-based security groups on an ongoing basis to ensure folks don’t have access to sectors they shouldn’t.
- With the growing importance of GDPR compliance and legislation, keep an eye on your baseline security posture and make sure to track any changes you notice routinely.
- There are more critical times to test your security environment than just your standard monthly tests. During implementation and testing, after adding new functionality, whenever a worker gets assigned to multiple groups (and thus, has access to numerous different security areas) or you make changes to security groups, you should always test to make sure those changes haven’t granted anyone inappropriate security access.
A Few Common Mistakes to Avoid
Let’s take a closer look at a few common security mistakes to avoid to save your team time (and money) in the long run…
Complicated Security Groups
The best piece of advice we can share (and share again) is to keep Workday Security simple. We’ve seen so many organizations get into the mode of making changes to fix every single issue only to realize that they’ve added so many new features that the system has more problems than when they started.
Keep your security solutions simple. When you create privacy and security restrictions, do your best to avoid a lot of intersections in Security with too many exclusions. Especially as you try to navigate your own change management plan as your company expands and employees come and go, simplifying who has access to what is important.
Managing change and troubleshooting issues with your data security is a key piece in your company’s general data protection regulation plan. Data protection is at the heart of your company’s success, so, simplifying this process can help save your employees, administrators, and the whole organization time, resources, and quite a few headaches.
Improper Setup for Integrations
When it comes to integrations within your Workday system, keeping it simple is your key to success. As soon as you complicate the process with an overload of information or limited access from improper account types, you introduce a new set of problems that could be easily avoided.
Too Much Information
A common mistake we’ve seen implementers make is throwing everything short of the kitchen sink into making an integration run, instead of narrowing things down to only the information it needs to run.
In other words, if you’re building an integration that requires Security for the integration to run, ensure the integration only has the access it needs to run its process and nothing more. Otherwise, you’re basically throwing broken glass in the road ahead of your car and hoping you don’t run over it later.
Not only will including too much information in one step of the process confuse you later on, but it could also make your implementation or integration process in Workday run more slowly. We all know that time is money, so being able to control the timeline of your business processes and keep track of integrations regularly is an important piece of your success, especially given the ever-changing data and security industry.
Issues with Personal User Accounts
Another way we’ve seen clients fumble their integrations is by allowing them to run under personal user accounts. We’ve seen situations in the past where an integration was set up to run under an individual user account. That worked…until the person left the company. As was the standard practice, the company disabled their account…which also caused the integration to fail.
Lessons like these can be time-consuming and frustrating for companies to learn, so understanding the proper ways to handle your integrations early is key.
Lack of Documentation
When it comes to security, documentation is critical. You need to develop a plan on how requests will come in, what will be reviewed and prioritized, and how work will get done, and you also have to document this plan. An undocumented program is like putting a jigsaw puzzle together after throwing away the box—you might have a clear picture of what you’re trying to accomplish right now, but what about a month from now? What ten months from now?
A well-documented plan will save you headaches in the future, not to mention ensure that everyone involved in the project has something they can reference as things progress. This way, each employee is held accountable for their responsibilities, and nothing slips through the cracks for someone else to fix later.
Forgetting a Comprehensive Testing Plan
Before you even start implementing Workday security, develop a comprehensive testing plan. Working proactively and setting up your testing plan beforehand will save you time (and maybe even some money) once you get to that point in the project. With a set testing plan, everyone involved knows 1) what to expect and 2) what is expected of them at that point in the project.
Unfortunately, setting up proper testing plans isn’t always at the top of the priority list. We’ve had clients in the past that failed to test every single change they’ve made, and somehow, it’s always the ones that seem fine at the beginning that have an enormous impact on every other aspect of security.
A comprehensive testing regimen will help you discover issues before they end up breaking the rest of your system.
Administrator Approval for Every Security Request
Finally, it’s important for your Workday Security administrator to have the ability to push back on security requests. If someone in the company makes a security change or request, review it and challenge it, if needed. Far too often, we’ve seen admins get in the habit of automatically approving every request that comes in.
If a security request isn’t valid, necessary, and tested, it shouldn’t be approved. This helps maintain your data privacy and protect even the most sensitive data in your systems. Using stricter approval criteria for Workday data security risks an essential factor in keeping your data secure and ensuring it stays in the right hands.
Properly optimizing your Workday Security configuration is critical to ensure your data isn’t compromised or misused. And, when it comes to rule breakers, our experienced team of Workday consultants can help you avoid risk and ensure top-notch protection through security groups, domain security, and implementing business process best practices.
How Can We Help?
If you need help with security permissions, optimization, or testing, our team of Workday experts can help. And, to help you gain some insight into who you could be working with, here’s an example profile of one of our best Workday Security consultants.
Surety Senior Workday Security Consultant
- 8+ years of overall Workday experience, all 8 years engrossed in Security as well
- Has successfully led two Security implementations and served other clients as the security expert, giving best practices, advice, knowledge transfer, etc.
- Has designed and implemented Security configuration for Eastern Europe and APAC regions
Experience configuring, reconfiguring, and teaching Security - Technical and functional oversight for the global Workday Human Capital Management system, including Security, Payroll, Benefits, Expenses, HR, and Finance
Contact us today to get started!



